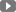In today’s digital era, safeguarding sensitive information has become more critical than ever. Data leakage protection (DLP) is a cornerstone of robust data security measures, designed to prevent unauthorized access and dissemination of sensitive data. This article will delve into the significance of data leakage protection, common causes of data breaches, DLP technologies, best practices for implementation, and the evolving role of data security experts in this landscape.
Mục lục
- 1 Significance of Data Leakage Protection
- 2 Common Causes and Examples of Data Breaches
- 3 Overview of Data Leakage Prevention (DLP) Technologies
- 4 Best Practices for Implementing an Effective DLP Strategy
- 5 The Role of Data Security Experts in Implementing DLP Strategies
- 6 Case Studies of Successful DLP Implementation
- 7 Future Trends in Data Leakage Protection
- 8 Conclusion
Significance of Data Leakage Protection

Data leakage protection is crucial for businesses of all sizes, as data breaches can have far-reaching consequences. Not only can they result in financial losses, but they can also damage a company’s reputation and erode customer trust. In today’s interconnected world, the impact of a data breach can extend beyond just one organization; it can affect other companies or individuals whose data may be linked to the compromised information.
Why Safeguarding Sensitive Information is Crucial
Data leakage can have devastating consequences for organizations and individuals alike. Unauthorized access to confidential information can lead to financial losses, reputational damage, and regulatory penalties. For organizations, a single data breach can result in millions of dollars in losses, not to mention the erosion of customer trust and loyalty. For individuals, compromised personal data can lead to identity theft and financial fraud. Furthermore, with the rise of privacy laws and regulations like the GDPR and CCPA, businesses are legally obligated to protect sensitive data and can face severe consequences for non-compliance.
Impact of Data Breaches
Data breaches can result in:
- Financial Losses: Both immediate costs (legal fees, regulatory fines) and long-term financial implications (loss of business, increased cybersecurity insurance premiums).
- Reputational Damage: Once trust is compromised, customers may take their business elsewhere.
- Operational Disruption: Recovery from a data breach often requires significant time and resources, hampering business operations.
- Legal Consequences: Failure to protect sensitive data can lead to lawsuits and non-compliance penalties.
Common Causes and Examples of Data Breaches
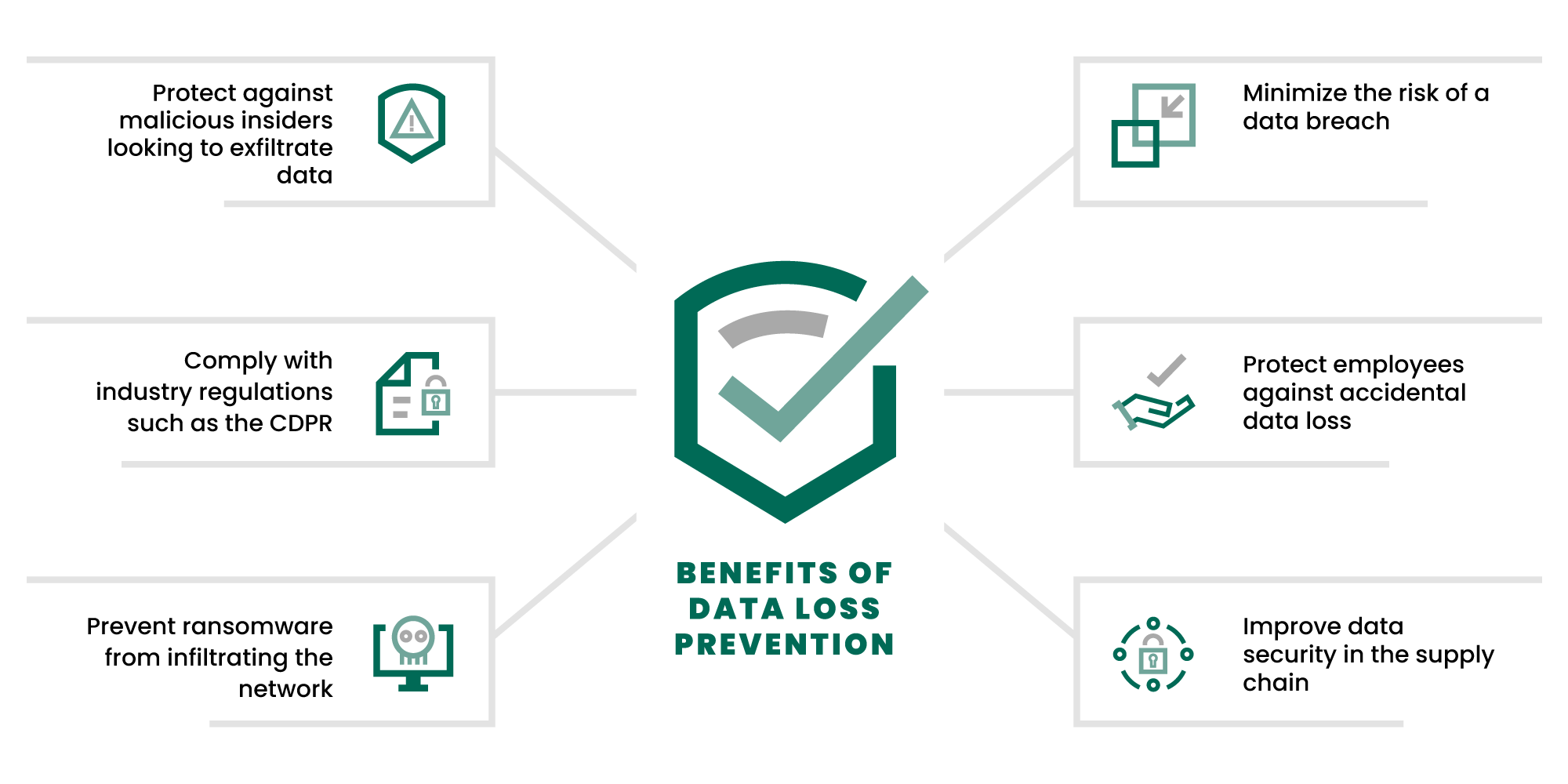
There are several ways in which data breaches can occur. Some of the most common causes include:
Analysis of Common Vulnerabilities
Understanding the root causes of data breaches is essential for preventing them. Common vulnerabilities include:
- Human Error: Misconfigured systems, inadvertent sharing of sensitive data, and lack of employee training.
- Insider Threats: Disgruntled employees or those unwittingly aiding data exfiltration.
- Weak Passwords and Authentication: Easily guessable passwords and inadequate multi-factor authentication (MFA).
- Malware and Phishing Attacks: Cybercriminals exploit these tactics to gain unauthorized access to networks and data.
- Insecure Network Connections: Especially in the era of remote work and BYOD (Bring Your Own Device) policies.
High-Profile Data Breaches
There have been several high-profile data breaches in recent years, highlighting the need for robust DLP measures. Some examples include:
- Equifax: In 2017, Equifax suffered a massive data breach that exposed personal and financial information of over 147 million customers.
- Marriott International: In 2018, Marriott International experienced a data breach compromising sensitive information of over 500 million guests.
- Capital One: In 2019, Capital One fell victim to a cyberattack that resulted in the theft of over 100 million customer records.
- Equifax (2017): Personal information of 147 million people was exposed due to a vulnerability in a web application.
- Yahoo (2013-2014): A breach impacting 3 billion user accounts due to outdated security measures.
- Target (2013): Credit/debit card information of 40 million customers was stolen through a compromised vendor.
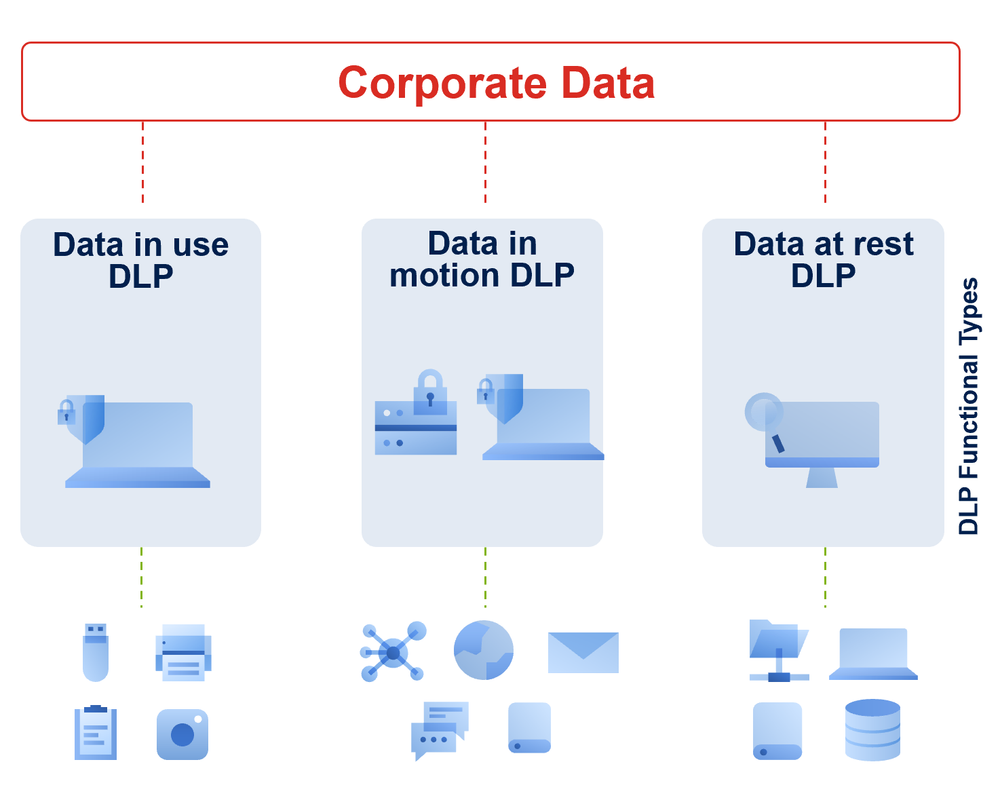
Overview of Data Leakage Prevention (DLP) Technologies
DLP technologies are designed to prevent data leakage by detecting and protecting sensitive information from unauthorized access.
What is DLP Technologies
DLP technologies use a combination of policies, processes, and tools to identify, monitor, and protect sensitive data. These solutions can be deployed as hardware or software and work to prevent data breaches by monitoring network traffic for potential leaks, enforcing security policies, and providing real-time alerts.
They operate at various levels:
- Network DLP: Monitors and protects data in transit across the network by analyzing traffic patterns and applying security policies to prevent unauthorized data transfers.
- Endpoint DLP: Controls data flow from endpoints such as laptops, desktops, and mobile devices. It ensures that sensitive information is not copied, printed, or transferred to unauthorized locations.
- Cloud DLP: Secures data stored in cloud services and applications by enforcing encryption, access controls, and compliance measures to prevent data breaches.
Types of DLP Solutions
- Content Inspection: Analyzes data at rest, in motion, and in use to identify and protect sensitive information. This includes scanning emails, files, and databases for confidential data and applying protective measures.
- Context-Based DLP: Uses contextual information (user behavior, device type, location) to make intelligent decisions about data protection. For example, it may allow data transfers within an office environment but restrict them when the user is accessing data remotely.
- Behavioral Analytics: Identifies unusual patterns that may indicate a potential data leak. By monitoring user activity and comparing it to established baselines, this type of DLP can detect anomalies such as large data transfers or access to sensitive information at odd hours, which may suggest malicious intent or a compromised account.
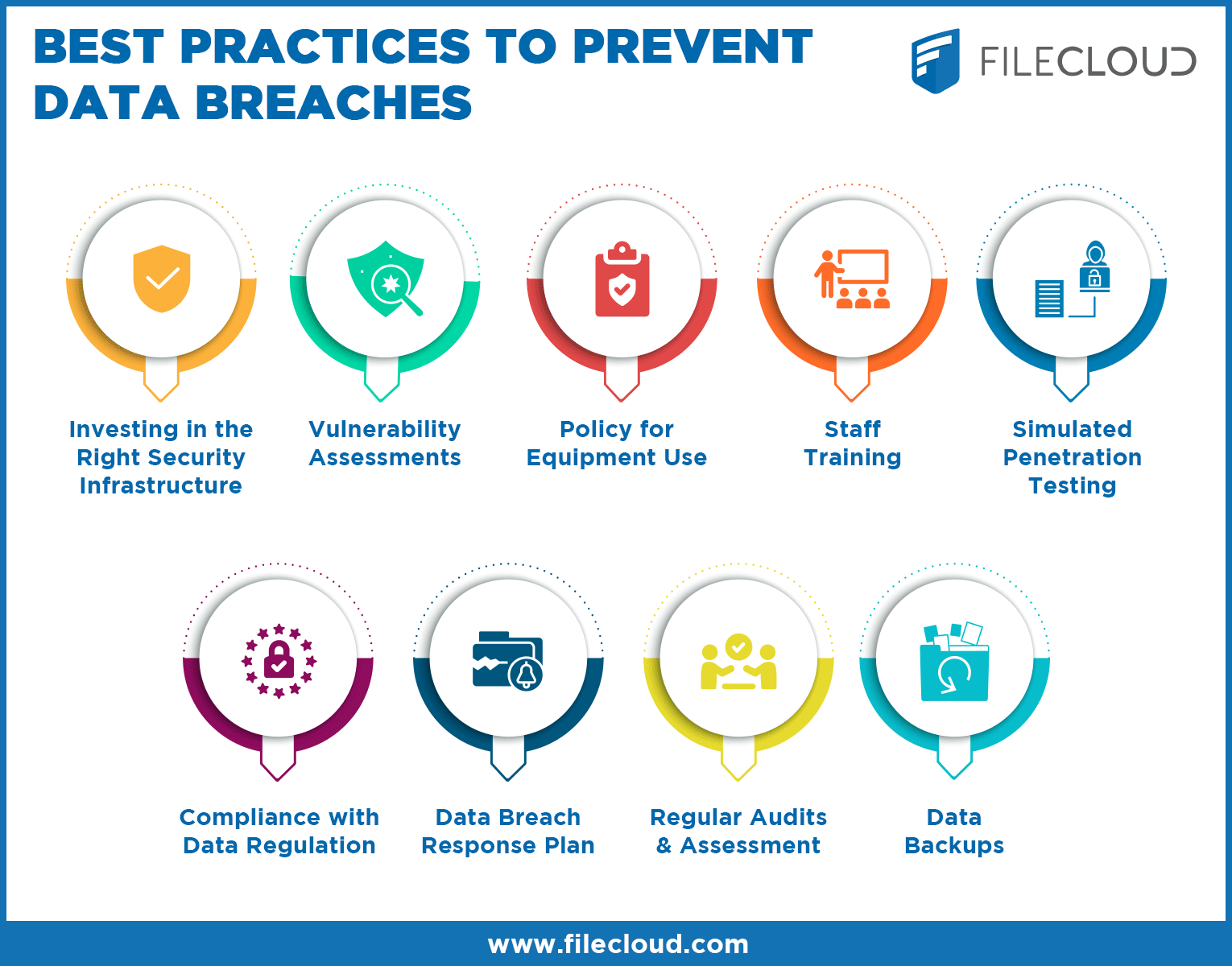
Best Practices for Implementing an Effective DLP Strategy
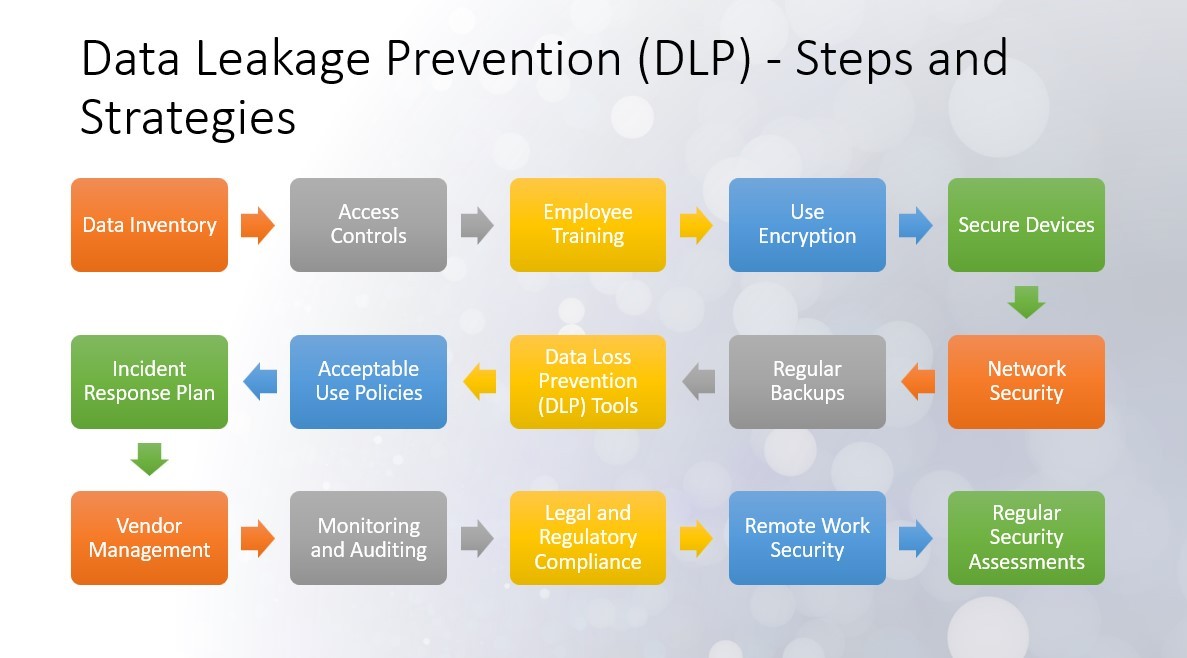
Guidelines for Developing a Robust DLP Plan
- Identify Sensitive Data: Understand what constitutes sensitive data within your organization.
- Classify Data: Use data classification tools to categorize data based on sensitivity and criticality.
- Set Policies and Rules: Define clear policies and rules on how data should be handled.
- Implement DLP Technologies: Deploy DLP solutions tailored to your organization’s needs.
- Regular Risk Assessment: Continuously monitor risks and update policies accordingly.
- Employee Training: Conduct regular training sessions to raise awareness about data security practices.
Importance of Regular Risk Assessment and Policy Updates
Regular risk assessments are crucial to identifying potential vulnerabilities and making necessary updates to security policies. As technology evolves, so do cybersecurity threats, and it’s essential to stay up-to-date with the latest risks and adapt accordingly.
The Role of Employee Training in DLP Strategies
Employees play a significant role in preventing data breaches, but they can also be a weak link if not properly trained on data security practices. Regular training can help employees understand their responsibilities when handling sensitive information and how to identify and report potential breaches.
The Role of Data Security Experts in Implementing DLP Strategies
Data security experts play a crucial role in implementing effective DLP strategies. They have the expertise and knowledge to assess an organization’s data security needs, identify potential vulnerabilities, and recommend the best DLP solutions. They also ensure that these solutions are properly implemented and regularly updated to adapt to evolving cybersecurity threats.
Benefits of Hiring Data Security Experts
- Specialized Knowledge: Data security experts have extensive knowledge and experience in cybersecurity, making them well-equipped to handle data protection.
- Identify Vulnerabilities: By conducting thorough risk assessments, data security experts can identify potential vulnerabilities that may go unnoticed by non-experts.
- Recommend Tailored Solutions: Data security experts can recommend DLP solutions tailored to the specific needs of an organization.
- Ensure Proper Implementation and Maintenance: Hiring experts ensures that DLP solutions are properly implemented and regularly updated to keep up with the evolving cybersecurity landscape.
Significance of Expertise in DLP Implementation
Data security experts play a crucial role in the successful implementation of DLP strategies. Their responsibilities include:
- Conducting Risk Assessments: Evaluating potential threats and vulnerabilities.
- Designing DLP Architectures: Developing comprehensive strategies tailored to the organization’s specific needs.
- Ensuring Compliance: Keeping abreast of regulatory requirements and ensuring the organization meets all standards.
Expert Insights
- “Data leakage prevention is not just about technology; it’s a strategic approach that requires understanding the business, its processes, and the data,” says John Doe, CTO of SecureTech.
- “Organizations need to adopt a proactive, not reactive, mindset towards data protection. This means staying ahead of emerging threats and leveraging the latest technologies,” advises Jane Smith, Data Security Analyst at GlobalGuard.
- “The human element is often the weakest link in data protection. Training and awareness programs are just as important as technology in preventing data leaks,” highlights Michael Davis, Chief Technologist at DataDefend.
- “A comprehensive DLP strategy should cover all aspects of data handling, including encryption, monitoring, and incident response,” suggests Alex Johnson, Director of Information Security at Fortress.
Case Studies of Successful DLP Implementation

Case Study 1: Financial Services Firm
A prominent financial services firm faced significant challenges in managing and protecting sensitive client information due to the sheer volume of transactions processed daily. By implementing an integrated DLP solution focusing on both network and endpoint security, the firm substantially reduced instances of data leakage. The solution provided real-time monitoring and alerts, enabling rapid response to potential threats. As a result, the firm not only secured client data but also achieved compliance with stringent financial regulations, enhancing client trust and safeguarding its reputation.
Case Study 2: Healthcare Organization
A large healthcare organization sought to protect patient records against unauthorized access and potential breaches. By incorporating context-based DLP and behavioral analytics, the organization could detect unusual patterns of data access that indicated a potential breach. The DLP solution was customized to align with healthcare regulations such as HIPAA, ensuring that patient data was handled correctly and securely. This proactive approach enabled the organization to prevent data breaches and maintain the confidentiality of sensitive health information.
Case Study 3: Global Manufacturing Company
A global manufacturing company faced challenges in securing intellectual property and trade secrets across multiple international offices. By deploying a cloud DLP solution, the company ensured that sensitive data was encrypted and protected no matter where it was accessed. The DLP system also included robust data classification and policy enforcement, which significantly decreased the risk of data loss. The successful implementation of the DLP strategy helped safeguard the company’s competitive edge and promoted secure collaboration across its global workforce.
Future Trends in Data Leakage Protection
As technology evolves, so do the methods and tactics used by cybercriminals to exploit vulnerabilities. To effectively protect against data leakage, organizations must adapt and stay ahead of these ever-evolving threats.
Emerging Technologies and Methodologies
As data protection needs evolve, so do DLP technologies and methodologies. Future trends include:
- AI and Machine Learning: Enhanced predictive capabilities to identify potential threats before they materialize.
- Zero Trust Architecture: A security model that assumes no trust and continuously verifies every request.
- Advanced Encryption Methods: Stronger encryption techniques to protect data at rest and in transit.
- Integrated Security Platforms: Solutions that provide comprehensive protection across various environments (on-premises, cloud, hybrid).
Predictions for the Future
The future landscape of data leakage protection promises to be shaped by several pivotal trends. These include:
- Behavioral Analytics: By deeply understanding user behavior and access patterns, future DLP solutions will be capable of detecting anomalies more effectively and reducing false positives. This predictive approach helps in identifying potential data breaches before they occur.
- Blockchain Technology: Leveraging blockchain’s inherent characteristics of immutability and transparency, businesses can ensure secure transactions and traceability of data, making it more difficult for unauthorized parties to alter or access sensitive information.
- Quantum Cryptography: As quantum computing becomes more prevalent, it will revolutionize encryption techniques, making data practically unhackable by traditional means. Quantum cryptography aims to provide unprecedented levels of data security.
- Regulatory Developments: Stricter data protection regulations worldwide, such as GDPR in Europe and CCPA in California, will continue to shape DLP strategies. Organizations will need to stay compliant with evolving legislation to avoid hefty fines and protect their reputation.
Conclusion
Data leakage protection is no longer a luxury but a necessity for modern enterprises. By understanding the significance of DLP, implementing best practices, and leveraging advanced technologies, organizations can safeguard sensitive information and maintain a competitive edge.
As we move forward, continuous improvement and adaptation to new trends will be crucial. For data security experts, the journey toward comprehensive data protection is ongoing, requiring vigilance, innovation, and a proactive approach.
In the words of John Doe, CTO of SecureTech: “Data leakage prevention is not just about technology; it’s a strategic approach that requires understanding the business, its processes, and the data.”
For organizations looking to bolster their data protection measures, now is the time to act. Prioritize your data security initiatives and invest in robust DLP strategies to protect your most valuable assets.